Big DataSec: A Checklist for Securing Data Lakes
MAY, 2023
by Andrew Walker
Author Andrew Walker
Andrew Walker is a software architect with 10+ years of experience. Andrew is passionate about his craft, and he loves using his skills to design enterprise solutions for Enov8, in the areas of IT Environments, Release & Data Management.
I. Introduction
In the digital age, data has become the lifeblood of modern businesses. As companies generate and store vast amounts of data (big data), the need for efficient and secure data storage solutions has never been greater. Data lakes have emerged as one such solution, allowing organizations to store, manage, and analyze large and varied datasets.
However, with the benefits of data lakes come significant security risks. Cyber attacks and data breaches have become increasingly common, and organizations must take necessary steps to secure their data lakes.
In this DataSec article, we’ll provide a checklist for ensuring the security of data lakes, highlighting the key security measures that organizations must implement to protect their data.
II. What is a Data Lake?
A data lake is a centralized repository that allows organizations to store and manage large volumes of structured and unstructured data. Unlike traditional data storage systems, data lakes can accommodate data from multiple sources, such as IoT devices, social media platforms, customer databases, and more. Data lakes enable organizations to perform advanced analytics, machine learning, and artificial intelligence on large and diverse datasets, driving insights and actionable intelligence.
Data lakes are typically built using cloud computing technologies, enabling organizations to scale their storage capacity quickly and efficiently. The data in a data lake can be stored in its native format, allowing for more flexibility and easier processing compared to traditional data storage systems.
However, because data lakes are often connected to the internet and store sensitive data, they can be vulnerable to cyber threats and data breaches. As such, it’s crucial for organizations to implement robust data security measures and regularly monitor their data lake for vulnerabilities and threats.
III. Access Control, Authorization, and Authentication
Access control is one of the most critical security measures for any data storage system, including data lakes. Access control involves restricting access to authorized individuals, ensuring that only those with the appropriate permissions can access the data stored in the data lake.
To implement effective access control, two key components are necessary: authentication and authorization. Authentication ensures that the person trying to access the data is who they claim to be. Authorization, on the other hand, determines whether the user has the necessary permissions to access the data.
By default, many employees in an organization are often granted access to cloud platforms and data lakes, leading to unnecessary vulnerabilities in the system. Therefore, implementing a well-guarded access control system is essential to restrict access to only authorized personnel.
An effective access control system should identify and verify who has access to the data and restrict access to a limited group of individuals. This helps to prevent unauthorized access and protect the data stored in the data lake.
IV. Platform Hardening
Platform hardening is another critical measure for ensuring data lake security. It involves minimizing the potential “attack surface” of the system, which refers to the number of ways that an attacker could exploit a vulnerability in the system to gain access to sensitive data.
To harden the platform, unnecessary cloud tools, ports, applications, and services connected to the data lake should be removed. Access to the data lake should also be restricted, and access controls should be configured for resource access and allocation. If the data lake sits on the cloud, only one cloud account should be created for application and software deployments.
Moreover, it’s essential to incorporate security standards and guidelines listed by the Computer Information Security (CIS) Center for Internet Security and other standardized data security boards. By following these guidelines, organizations can ensure their data lake is secure and protect against common attack vectors.
Platform hardening ensures that the data lake is less vulnerable to attacks and helps prevent unauthorized access, data breaches, and other cyber threats.
V. Data Lineage
Data lineage refers to the process of tracking the movement of data within a data lake. In a data lake, data comes from various sources and is stored in its raw form. This makes it challenging to keep track of where the data is coming from, how it’s being used, and where it’s going.
Data lineage creates a map of the data, enabling organizations to track the data’s flow and identify any risks or gaps within the data lake. With data lineage, organizations can know when, by whom, and where the data is moving/accessed. This helps track the data flow and identify any risks or gaps within the data lake.
Data lineage is essential in identifying the origin of data, identifying who has access to it, and how it’s being used. By keeping track of data lineage, organizations can prevent unauthorized data access and ensure data accuracy and completeness. Additionally, data lineage helps organizations to comply with data protection regulations and meet auditing requirements.
VI. Host-Based Security
Host-based security is a security measure that involves securing the host system, including servers and endpoints. It involves implementing intrusion detection algorithms, audit trails, and log management to detect any unusual activity or access requests.
Intrusion detection algorithms identify anomalous activities or access requests and notify the relevant authorities. These activities may be internal, coming from within the organization network, or external, coming from an external attacker. By implementing intrusion detection algorithms at the host level, organizations can detect anomalous activities and prevent unauthorized access to the data stored in the data lake.
Log management and intrusion detection algorithms are both critical components of host-based security. Collecting and managing logs can be exhaustive on resources such as storage. Therefore, having an intrusion detection system can help detect anomalies without taking up resources. By combining intrusion detection algorithms, log management, and other host-based security measures, organizations can ensure their data lake is protected from cyber threats and unauthorized access.
VII. Implement RBAC & IAM Solutions
Implementing Role-Based Access Control (RBAC) and Identity Access Management (IAMIAM) solutions is another critical measure for ensuring data lake security.
RBAC involves defining user roles and permissions based on their job responsibilities. It enables organizations to restrict access to specific resources based on the roles and responsibilities of individual users. By using RBAC, organizations can control access to sensitive data and prevent unauthorized access.
IAM, on the other hand, involves managing user identities and their access to resources. It enables organizations to grant, revoke, or modify user permissions based on their role and responsibilities. IAM solutions typically involve multi-factor authentication, which adds an additional layer of security to the system.
Implementing RBAC and IAM solutions is critical in large organizations with multiple departments and varied job roles. It enables organizations to control access to specific resources and prevents unauthorized data access. By combining RBAC, IAM, and other access control measures, organizations can ensure their data lake is secure and protected from cyber threats.
VIII. Data Encryption
Data encryption is another crucial security measure for ensuring data lake security. Encryption involves encoding data using a specific algorithm and key, making it unreadable to anyone without access to the key.
If an unauthorized user gains access to encrypted data, they will not be able to read it without the encryption key. Data encryption provides a layer of security against malicious attacks, data breaches, and other cyber threats.
For data lakes that sit on the cloud, it’s essential to follow the encryption guidelines recommended (and in most cases, provided) by the cloud service provider. On-prem data lakes must be secured with data encryption policies as dictated by standard security organizations.
Encryption can be done at all levels of data storage systems, such as files, tools, applications, and databases. By encrypting the data stored in the data lake, organizations can ensure that even if it’s accessed by unauthorized users, the data will remain protected.
Encryption, combined with other security measures such as RBAC, IAM, and access control, can provide a robust data protection layer that helps prevent unauthorized data access and protect the data lake from cyber threats.
IX. Network Perimeter
Network perimeter security is another critical security measure for ensuring data lake security. Network perimeter security involves protecting the organization’s network with strong security protocols to prevent cyber threats and restrict hackers.
Firewalls are an essential component of network perimeter security. They act as sieves, allowing only certain traffic to flow into the organization’s network, which helps to restrict the flow of traffic that might potentially harm the network.
Intrusion detection and prevention algorithms are also an efficient way of identifying and restricting anomalous events. They use advanced machine learning algorithms to identify threat profiles or activities and notify the relevant authorities.
Other measures such as border routers, virtual private networks (VPNs), and network segmentation can also be used to secure the network perimeter. By securing the network perimeter, organizations can prevent unauthorized access to the data lake and protect it from cyber threats.
In summary, securing the network perimeter is critical for protecting the organization’s data lake. By implementing firewalls, intrusion detection and prevention algorithms, and other network perimeter security measures, organizations can ensure their data lake is secure and protected from cyber threats.
X. Data Lake Security Checklist
To summarize the key points discussed, here’s a data lake security checklist that organizations should consider to ensure their data lake is secure:
Access Control, Authorization, and Authentication: Implement access control protocols to identify and verify “who” has access to the data lake and restrict access to limited people.
Platform Hardening: Remove unnecessary cloud tools, ports, applications, and services connected to the data lake. Configure access controls for resource access and allocation. Follow security standards and guidelines enlisted by the Computer Information Security (CIS) Center for Internet Security and other standardized data security boards.
Data Lineage: Keep track of where the data is originating, how and who is using it, its movement in the data lake, and so on. Data lineage creates a map of the data, enabling organizations to track the data flow and identify any risks or gaps within the data lake.
Host-Based Security: Implement intrusion detection algorithms, audit trails, log management, and other measures to secure the host system and detect anomalous activities or access requests.
Implement RBAC & IAM solutions to grant access and keep track of resource controls.
Data Encryption: Encrypt data at all levels of data storage systems to protect it from unauthorized access.
Network Perimeter: Secure the network perimeter with firewalls, intrusion detection and prevention algorithms, and other measures to prevent cyber threats and restrict hackers.
By following this checklist, organizations can ensure that their data lake is secure and protected from cyber threats, unauthorized access, and data breaches.
Enov8 : Manage your IT Landscape: Risk Screenshot
XI. Leveraging Enov8
Enov8 offers comprehensive solutions to help manage your IT footprint & data security concerns, including its IT Environment Management and Test Data Management solutions.
Enov8 Environment Manager enables organizations to gain a better understanding of their IT landscape and manage it more effectively. Its out-of-the-box modeling capabilities, coupled with system security information capture, facilitate planning, coordination, and incident management. Additionally, it offers orchestration through automation and provides real-time insights across the IT fabric. By leveraging Enov8 Environment Manager, organizations can streamline their IT operations, enhance system security, and improve their overall IT performance.
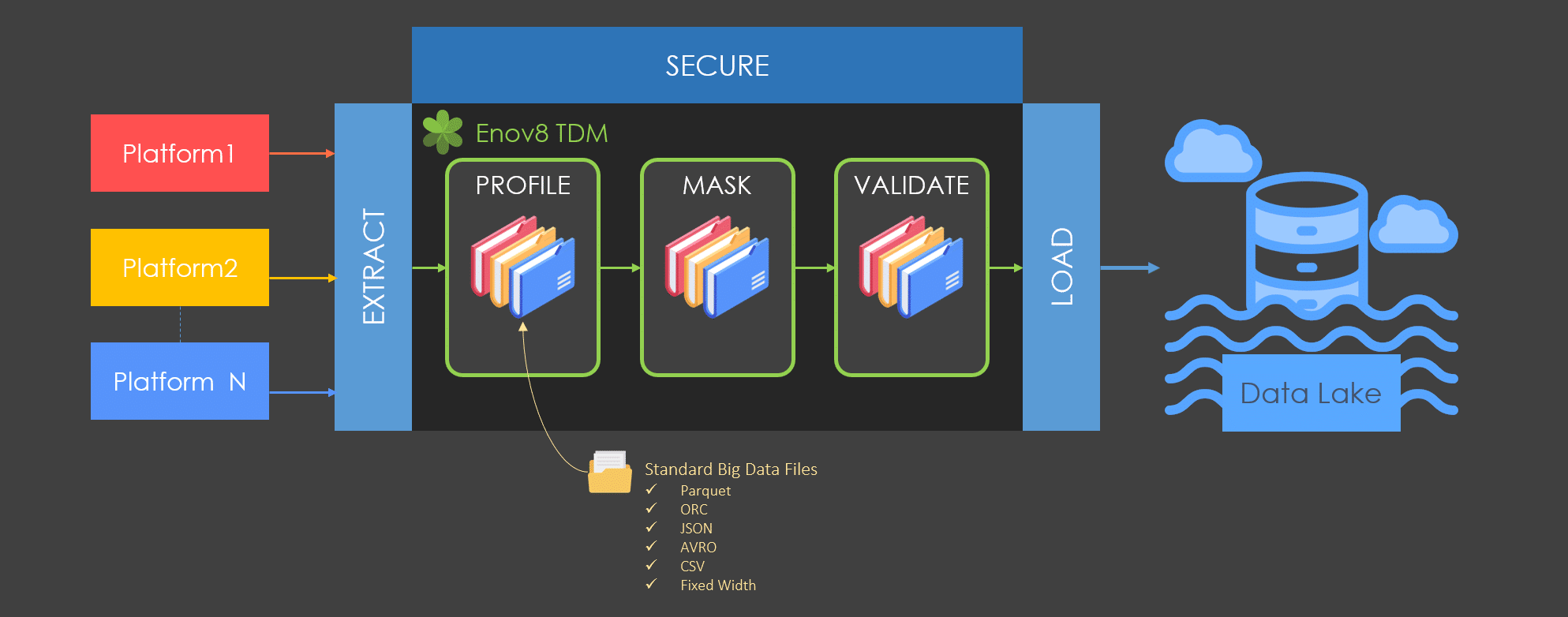
Enov8 Test Data Manager (aka Data Compliance Suite) is another solution that compliments the needs of data security and data privacy by providing data profiling for risk discovery, data masking for obfuscation, and compliance validation methods. By leveraging Enov8 Test Data Manager in conjunction with Enov8’s IT environment management and data security platform, organizations can further strengthen their data security measures and protect their data more effectively.
XII. Conclusion
In conclusion, the exponential growth of data generation has made data storage repositories such as data lakes and cloud computing technologies indispensable for organizations. However, data security has become a major concern for organizations as cyber threats and data breaches have become increasingly common.
To mitigate these risks, organizations must take measures to ensure their data lakes are secure and functional at all times. The checklist provided above, covering access control, platform hardening, data lineage, host-based security, RBAC and IAM solutions, data encryption, and network perimeter, serves as a comprehensive guide for securing data lakes.
Furthermore, leveraging platforms such as Enov8 can enable organizations to manage their IT environments and data security more effectively. Enov8 provides a centralized platform for IT environment management and data security, enabling organizations to gain a comprehensive view of their IT environment, plan and coordinate changes more effectively, automate their IT environment and data changes, and protect their data from cyber threats.
Overall, securing data lakes is essential for building a strong development and deployment pipeline, which is crucial for business growth. Therefore, organizations must prioritize data security and implement the right measures and security policies to protect their data.
Other DataReading
Enov8 Blog: What s Data Friction from the Perspective of TDM
Enov8 Blog: What is Data Masking? And how do we do it?
Enov8 Blog: A DevOps Approach to Test Data Management
Relevant Articles
Smoke Testing: A Detailed Definition and Guide
In the realm of software development, ensuring the reliability and functionality of applications is of paramount importance. Central to this process is software testing, which helps identify bugs, glitches, and other issues that could mar the user experience. A...
What is Observability? A Foundation for SRE
Site Reliability Engineering (SRE) is a methodology for building and maintaining large-scale, highly available software systems. It involves applying software engineering practices to operations in order to increase reliability, reduce downtime, and improve the...
What is Ansible? A Detailed Guide for Dummies
As IT & Test environments become increasingly complex and dynamic, IT professionals need tools that can help them manage the complexity and ensure consistency across systems. Ansible is designed to address these challenges. In this post, we’ll provide an...
Database Virtualization Tools: 9 to Know About in 2026
Organizations evaluating database virtualization tools are usually trying to solve a very practical problem: how to give teams fast, safe access to realistic data without copying production databases over and over again. Whether the driver is test automation,...
Enterprise Release Management: A Comprehensive Guide
Enterprise Release Management (ERM) is a set of end-to-end practices that enable large organizations to effectively manage software releases. ERM is uniquely designed for the challenges of multiple teams building and releasing software simultaneously. ERM establishes...
Your Essential Test Environment Management Checklist
“Test Environment Management Checklist.” Yep, that sounds like a mouthful, but don’t let that discourage you. The idea here is quite simple—adopting a checklist to evaluate the soundness of your test environment management approach. Even though the idea sounds simple...